Tuesday, April 5, 2011
Epic Breach of Email Lists - Epsilon Data Management
Epsilon Data Management, subsidiary of Plano, Texas-based Alliance Data Systems, is a major multichannel marketing group, and calls itself "the world's largest permission-based email marketing provider", have recently admitted to a security breach which comprimised the email addresses of millions of users. While nothing more than names and email information was leaked, unfortunately a lot of people across the internet are going to have to expect a surge in spam email.
Epsilon supposedly sends out over 40 billion emails annually, and counts over 2,500 clients, 7 of which are Fortune 10 companies which allow Epsilon to host their customer databases.
According to Securityweek.com:
"Some may dismiss the type of data harvested as a minor threat, but having access to customer lists opens the opportunity for targeted phishing attacks to customers who expect communications from these brands. Being able to send a targeted phishing message to a bank customer and personally address them by name will certainly result in a much higher “hit rate” than a typical “blind” spamming campaign would yield. So having access to this information will just help phishing attacks achieve a higher success rate."
You can keep up-to-date on this breach of security with updated lists of corporations affected at SecurityWeek.com.
http://www.securityweek.com/massive-breach-epsilon-compromises-customer-lists-major-brands
Also, here are some other sources of information concerning the breach:
http://nakedsecurity.sophos.com/2011/04/04/epsilon-email-address-megaleak-hands-customers-customers-to-spammers/
http://www.washingtonpost.com/blogs/faster-forward/post/epsilon_mail_marketing_firm_exposes_millions_of_names_addresses/2011/04/04/AFEPbabC_blog.html
To setup email filtering and security services for your small to medium-sized business, please contact us at Cavu Networks to get started and prevent the hassle of being on the receiving end of spam and undesireable emails.
Wednesday, March 30, 2011
Office and Outlook Corrupt Installations - Missing Files
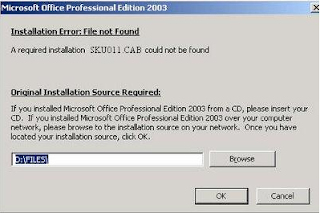 Every so often we must upgrade our Office or Outlook products to the latest and greatest version, or uninstall a product we no longer use because we've switched over to a new solution. Sometimes when we go to remove, repair or upgrade Microsoft Outlook or Office we run into a snag where the system tells us it cannot complete the function without the missing file known as SKU011.CAB, because it cannot be found.
Every so often we must upgrade our Office or Outlook products to the latest and greatest version, or uninstall a product we no longer use because we've switched over to a new solution. Sometimes when we go to remove, repair or upgrade Microsoft Outlook or Office we run into a snag where the system tells us it cannot complete the function without the missing file known as SKU011.CAB, because it cannot be found.The dialogue window which opens can be misleading, telling us we need to place the installation source disc in the machine and browse to where the missing file is located. If you are like some small to medium-sized businesses which have just recently gotten around to focusing on updating your software products, you may find that the original discs have gone missing, or the IT personnel you used when the business was a fresh start have disappeared or are no longer the same folks you use to perform your technology duties, and the software actually was with them.
In the case above, there is actually a simple and easy way to work around this issue by modifying the Windows registry. This corrupt installation issue is actually due to a value in the registry not being "0".
Now, before attempting to modify any registry data, check to see if you have staff comfortable doing this task as it can wreck your Windows profile if changes are made in error or if items are deleted by accident. Windows registry is no joke, it is literally a database of all the different components which Windows uses to function properly. Check to see if you have an assigned IT person, and if not, backup your registry before modifying any registry keys.
FIRST: BACKING UP WINDOWS REGISTRY DATA:
To backup Windows registry is a very simple matter which takes only a minute or two. Any time you need to edit the registry, you go to Start > Run, and in the dialogue box type "regedit" (without the quotation marks), and press Enter.
-
Open the Registry Editor by clicking the Start button
 , typing regedit into the Search box, and then pressing ENTER.
, typing regedit into the Search box, and then pressing ENTER.  If you are prompted for an administrator password or confirmation, type the password or provide confirmation.
If you are prompted for an administrator password or confirmation, type the password or provide confirmation. -
Locate and click the key or subkey that you want to back up.
-
Click the File menu, and then click Export.
-
In the Save in box, select the location where you want to save the backup copy, and then type a name for the backup file in the File name box.
-
Click Save.
-
Although you can back up more than the registry key or subkey that you are modifying, doing so adds to the size of the backup file.
-
Before editing the registry, it's a good idea to create a restore point using System Restore. The restore point contains information about the registry, and you can use the restore point to undo changes to your system. For more information, search Help and Support for "System Restore."
Fixing The Irritating Missing File Issue:
1. Click on your Start menu and select “Run…”
2. Once the dialogue box appears, type in 'regedit' and click “OK”
3. In the left tree structure, navigate to HKEY_LOCAL_MACHINE -> Software->Microsoft -> Office -> 11.0 -> Delivery.
4. There should be one entry under Delivery folder (e.g. {91E30409-6000-11D3-8CFE-0150048383C9} ), select that directory. (Don't select any other directory but this one, as this is specific to the issue shown at the top! If you cannot find it or are unsure, consult an IT professional!)
5. On the right side of the window, right-click on CDCache and select the first menu item ‘Modify’.
6. An ‘Edit String’ dialogue box will appear on your screen. Make sure to note the current value in this box incase you want to revert the changes that you have made. Change the value in the ‘Value Data:’ field to 0 and click ‘OK’. Once this is done, your registry will have been updated.
7. This completes the necessary changes that need to be made in order to fix the error message that appears in figure 1. Now that you are done, close all the windows that you opened and restart your Microsoft Office product.
An excellent resource for screenshots so that you may follow the steps visually can be found here at http://www.sku011cab.com/
Now you should be able to add/remove, change, repair or upgrade the Office product without that nasty error popping up.
Again, make sure you or someone in your office is comfortable backing up and modifying the registry data, it could save you much time and frustration going forward!
Tuesday, March 1, 2011
Clickjacking on Facebook
Lots of people follow celebrity goings-on and are excited when they think they're being directed via a Facebook fan-page to a rare video clip or photo which wasn't published through the normal, official channels. Because of this, misuse of such false links has become viral.
As explained in the following article by Sophos, a user can more easily protect themselves by installing the "NoScript" add-on for Firefox and the similar "NotScripts" for Google's Chrome browser. This allows you to choose when and where you want scripts to run so if you catch yourself on a page which looks a bit ...off...or not what you expected when you clicked the link to take you there, it is already blocking scripting until you give it the OK.
- Matthew Siers
*****************************************************
http://nakedsecurity.sophos.com/2011/03/01/lost-all-respect-for-emma-watson-facebook-clickjacking-attack-spreads-virally/
From Sophos' Naked Security: News. Opinion. Advice. Research
Lost all respect for Emma Watson? Facebook clickjacking attack spreads virally
![]() Over 30,000 people are part of the Sophos community on Facebook. Why not join us on Facebook to find out about the latest internet and Facebook security threats. X
Over 30,000 people are part of the Sophos community on Facebook. Why not join us on Facebook to find out about the latest internet and Facebook security threats. X
![]() Hi fellow Twitter user! Follow our team of security experts on Twitter for the latest news about internet security threats. X
Hi fellow Twitter user! Follow our team of security experts on Twitter for the latest news about internet security threats. X
![]() Don't forget you can subscribe to the SophosLabs YouTube channel to find all our latest videos. X
Don't forget you can subscribe to the SophosLabs YouTube channel to find all our latest videos. X
![]() Hi there! If you're new here, you might want to subscribe to the RSS feed for updates. X
Hi there! If you're new here, you might want to subscribe to the RSS feed for updates. X
Filed Under: Featured, Social networks, Spam
Emma Watson, the actress who plays the part of Hermione Granger in the Harry Potter movies, has found herself the subject of a clickjacking scam on Facebook.
Users of the social network have seen messages posted by their online friends claiming to have lost all respect for Emma Watson, after watching a video starring the young actress.

I lost all respect for Emma Watson when I seen this video! Outrageous!
If you're curious enough to click on the link, your browser will be taken to a webpage which pretends to be a YouTube-style video site called FbVideo.

If you've got this far, you'll probably be tempted to click to view the video. However, like the many clickjacking attacks we saw on Facebook last year, you will be invisibly clicking on a "Like" button without your knowledge, sharing the link further with your friends.
The page is designed to display a survey scam, which both earns money for the scammers and can trick you into handing over your mobile phone number to sign you up for a premium rate SMS service.
You can protect yourself from clickjacking threats like this by using browser plugins such as NoScript for Firefox.
But wouldn't it be great if Facebook required users to confirm that they wished to "Like" a webpage? That would make scams like have a harder time spreading virally via the social network.
By the way, other versions of the scam are using the names of Miley Cyrus.

If you find you have accidentally "Liked" an offending webpage, remove references to it from your wall and check your profile settings.
As Chet pointed out with a similarly-themed Justin Bieber clickjacking scam on Facebook, it can also make sense to logout from Facebook when you are not actively using it to reduce the chances of you being tricked into "Liking" things you don't really like.
If you're a Facebook user and want to keep up on the latest threats and security news why don't you join the Sophos Facebook page?
You could also do a lot worse than check out our best practices for better privacy and security on Facebook guide.
About the author
Graham Cluley is senior technology consultant at Sophos. In both 2009 and 2010, the readers of Computer Weekly voted him security blogger of the year and he pipped Stephen Fry to the title of "Twitter user of the year" too. Which is very cool. His awards cabinet bulging, he was voted "Best Security Blogger" by the readers of SC Magazine in 2011. You can contact Graham at gc@sophos.com, or for daily updates follow him on Twitter at @gcluley.Tuesday, February 15, 2011
Major Changes at Facebook, Be Prepared!
Unfortunately, there is a general misunderstanding of the proper use of privacy settings and overall social-network security. Even if you have your account locked down with privacy settings you feel safe with, those in your networks often do not, and these people have access to your page.
To read more detail about the upcoming changes, please check out the article written at Sophos below.
http://nakedsecurity.sophos.com/2010/11/15/faq-security-and-facebooks-new-messages-system/
Monday, February 14, 2011
Outbreak: United Parcel Service notification malware attack
- John
Thursday, February 10, 2011
That's Not Pizza In The Oven! - Interesting Approach to a Printer Fix
Even as an IT professional, this will occur once in a while. Sometimes you're given a 'bricked' device to dispose of or fix.
One client of ours had a failed printer, and after much poking, prodding and analyzing we simply couldn't get a response from the printer which was recognizable in the support documentation. The light status was completely wonky and in order to get further support assistance, we'd have had to spend money. However, John got online and did further due-diligence and discovered that this particular printer has a very interesting resolution for the symptoms we were seeing.
The printer is a HP Laserjet P2015dn. Apparently the formatter board on this model often fails as the lifetime of the machine progresses. We found some suggestions that you can remove the circuit board from this thing, and bake it in the oven for 8 minutes at 350 degrees, it would fix the problem. The heat softens the soldering so that it flows just enough to improve the connection of the circuitry. John rolled up some aluminum foil and placed it on the four points of the board to keep it off of the cookie sheet itself.
Yesterday we were laughing about this solution he found online. I thought to myself: "No way: this sort of thing has got to be a prank." I was wrong! Today I re-attached the formatting board he baked last night, and the printer is now functioning as expected. Go figure.
Monday, October 4, 2010
Is Comcast helping fake-AV criminals?
http://www.sophos.com/blogs/chetw/g/2010/10/04/comcast-provide-opportunities-fake-av/
